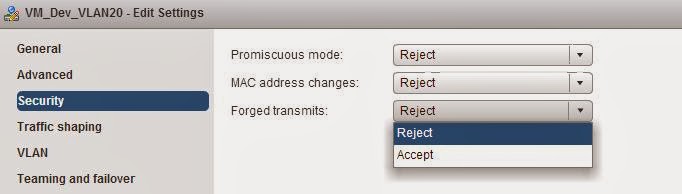
Default Security Settings for all the below 3 settings (Promiscuous mode, MAC address changes & Forged Transmits is set to Reject) in distributed Virtual Switch.
Promiscuous mode = Reject
MAC address changes = Reject
Forged Transmits = Reject
Default Security Settings of Standard Switch will be different than the dvswitch setting. In standard Switch, Below are the default settings:
Promiscuous mode = Reject
MAC address changes = Accept
Forged Transmits = Accept
Promiscuous Mode
Accept: If you set dvportgroup Security setting (Promiscuous mode to Accept), Virtual Machine adapter connect to this port group, will receive all frames passed on the switch in compliance with the VLAN policy of the port. This settings can only be useful in Firewalls, Intrusion detection systems and also in Packet capturing software. You can run packet capturing software like wireshark on the Guest operating system of the virtual machine connected to the port group with Promiscuous mode is set to Accept to capture the frames passing on that switch for network troubleshooting and analysis.
Reject: If you set dvportgroup Security setting (Promiscuous mode to Reject), Virtual Machine adapter will not receiving frames which is send for other virtual machines. By default, Promiscuous mode is set to reject. Don’t set it to Accept unless and until it is required. Enabling promiscuous mode without any prominent use will create a unnecessary load on the virtual machines.
MAC Address Changes
MAC address is a unique number assigned to networking components like Network adapters. Each virtual machine will be assigned with atleast one virtual network adapter (vNIC). each vNIC will be assigned with a MAC address when VM powers on first time. MAC address of the Virtual network adapter will be saved in the virtual machine configuration file (.VMX).which will be stored in the virtual machine directory on your datastore. The MAC address which is saved in .VMX file aslo termed as Initial address.
Usually this initial address will be copied by the Guest operating system to the network adapters as effective address unless you have bind some other MAC address at Guest OS level. Binding MAC address at Guest OS level will be useful when performing the P2V migration of the physical server in which installed application license is bind to the MAC address of physical host. This application will not work with other MAC address. In that case ,you can manually assign MAC address to network adapter inside the Guest operating system.
Runtime address is the address which is viewed by a port on the virtual switch. Runtime address will be same as the effective address which is assigned by Guest operating system.
Accept: If you set MAC Address Changes policy to accept and the guest operating system changes the MAC address of a virtual network adapter other than the address specified in the .VMX (virtual machine configuration file)(Initial address), The switch allows the inbound frames to pass with the new address. In other terms, If initial address is not same the effective address,this policy allows the frames to pass the switch if this security policy is set as Accept.
Reject: If you set MAC Address changes to Reject and the Guest operating system changes the MAC address of the virtual network adapter other than the address specified in the .VMX file (Initial address), the switch drops all the inbound frames to that virtual machine adapter In other terms,. If initial address is not same the effective address,it does not allow incoming traffic to the VM.
Forged Transmits
Forged Transmits works as same as the MAC address changes policy. Only difference is it works on Outgoing traffic whereas MAC address changes works on Incoming traffic
Accept: If the Forged Transmits is set to Accept, Switch does not perform any security filtering and permits all the outbound frames from the virtual machine network adapter even if the source MAC address is different from the one saved in virtual machine configuration file (.VMX)
Reject: If the Forged Transmits is set to Reject, Switch drops any outbound frames from the virtual machine network adapter, if the source MAC address is different from the one saved in virtual machine configuration file.
I hope this is informative for you. Thanks for Reading!!!. Be Social and share it in social media, if you feel worth sharing it.