VMware published a security advisory for CVE-2020-3952, describing a “sensitive information disclosure vulnerability in the VMware Directory Service (vmdir)”. vCenter Server 6.7 (embedded or external PSC) prior to 6.7u3f is affected by CVE-2020-3952 if it was upgraded from a previous release line such as 6.0 or 6.5.
Clean installations of vCenter Server 6.7 (embedded or external PSC) are not affected.
This vulnerability was published by VMware in April 2020 with a maximum CVSS score of 10.0. It allows an attacker with a network connection to take control of the vCenter Directory (and thus to the vSphere deployment).
VMware released a fix for this bug in vCenter Server 6.7 Update 3f for this vCenter Vulnerability. Any unpatched vCenter 6.7 that has been upgraded from a previous version is vulnerable to this attack. Please take a look at the article VMware Security Advisory (VMSA) VMSA-2020-0006.
You can also take a look at
How to Upgrade vCenter 6.7 to vCenter 7.0
Difference between vSphere 6.7 and vSphere 7.0
The vulnerability received a CVSSv3 score of 10 out of 10. Which means this is a very serious security issue. This also means you should patch your vCenter Server environment as soon as possible to address this vCenter Vulnerability.
An update has been released to address this sensitive information disclosure vulnerability by VMware in the form of VMware vCenter Server 6.7 U3f.
In this article, we will take a look at how to patch the vCenter server 6.7 to vCenter 6.7 U3f from the vCenter server appliance VAMI console to address this Vulnerability found in vCenter 6.7.
How to Perform vCenter Vulnerability Patching – Upgrade to vCenter 6.7 U3f
If you are using external PSC deployment, You need to patch the external PSC first and then followed by the vCenter server. In my example, I have a vCenter Server with embedded PSC.
Log in to the vCenter server appliance admin console using the URL https://<vCenter Server IP or hostname>:5480. with root credentials.
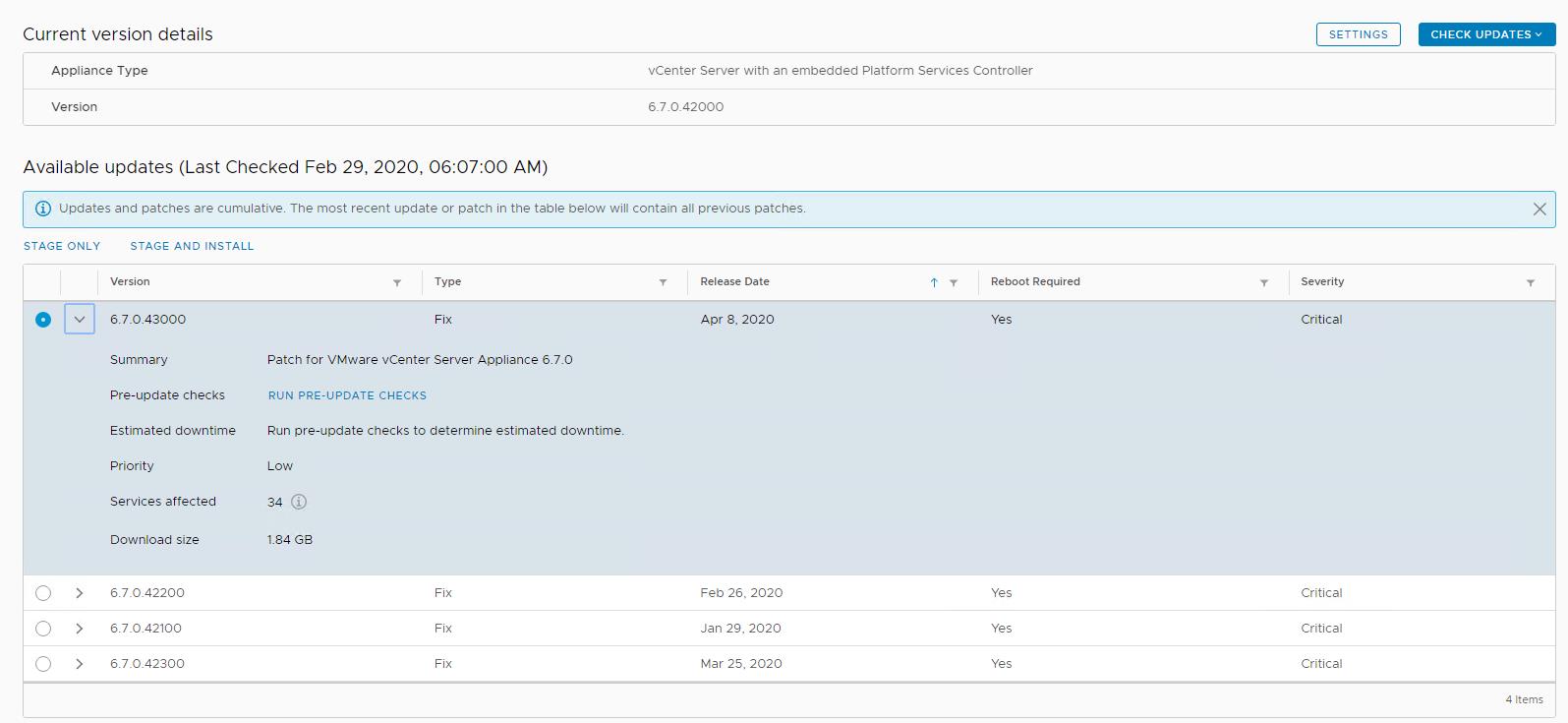
Click on Update -> Check Updates. Based on the current version of vCenter Server, it recommends multiple patches.
Select the vCenter patch version “6.7.0 43000” and the release date is “Apr 8 2020”. Click Stage and Install.
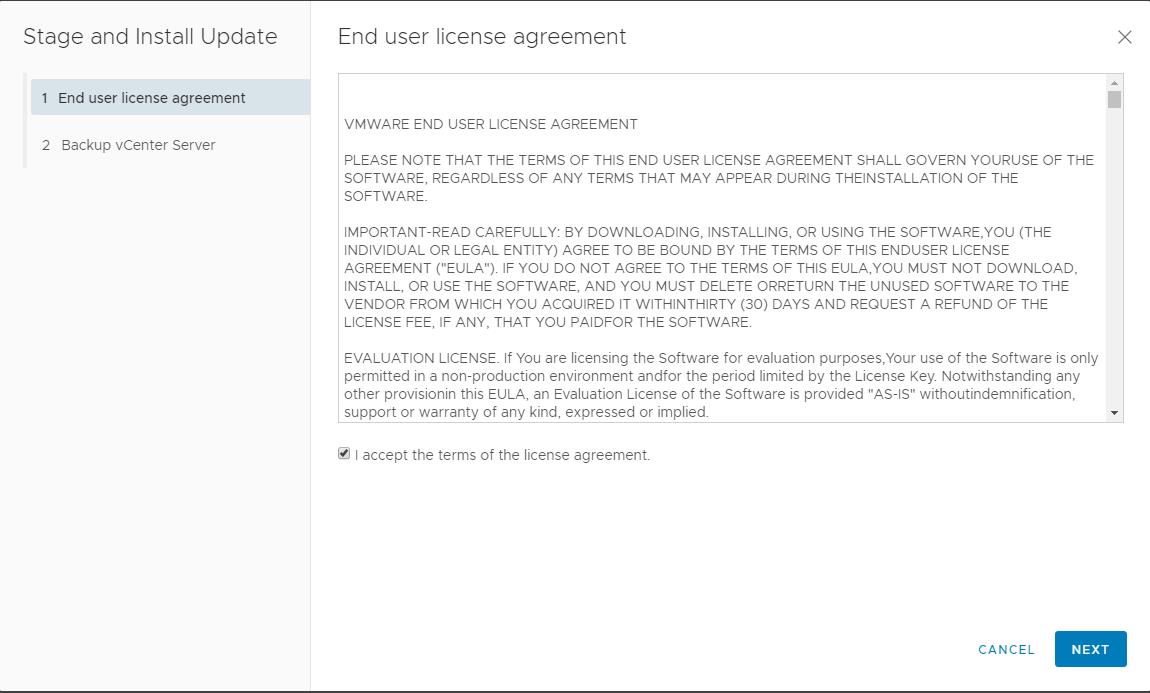
Accept the end-user license for installing the update for the vCenter server -> Click Next.
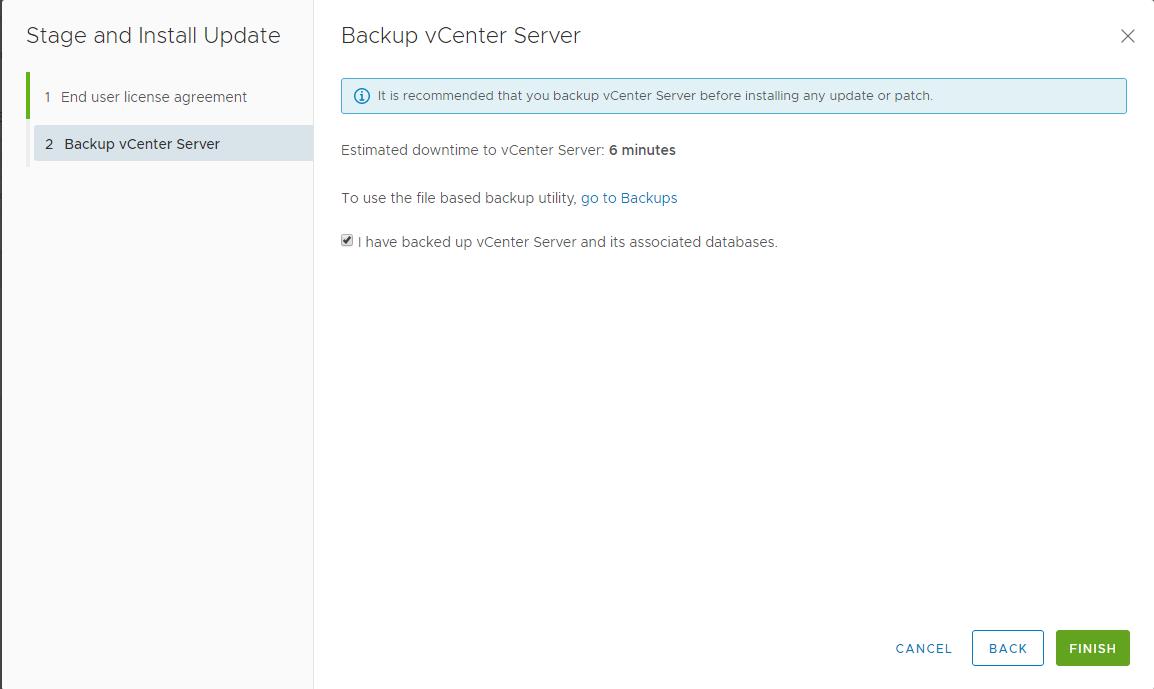
I would recommend to take the snapshot of the vCenter server appliance VM and also ensure you have the latest backup for the vCenter server. I have the latest backup for my vCenter server appliance. If you also have the backup -> Select the tickmark ” I have backed up vCenter server and its associated databases“. Click Finish.
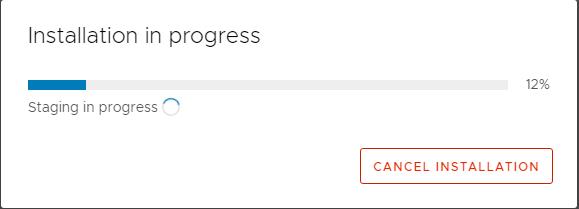
It will take a few minutes to complete the installation of the Update.
Installation is completed within a few minutes. Click Close. vCenter Server appliance will reboot after the patch installation.
Once the installation is completed, login to the vCenter Server VAMI console and ensure the version is 6.7.0 43000.
That’s it. We have completed patching the vCenter within few clicks to fix the vulnerability “CVE-2020-3952” found in vCenter server 6.7. I recommend everyone to update the vCenter server 6.7 to the latest build (vCenter 6.7 U3f) to address this vulnerability. I hope this article is informative for you. Thanks for Reading!!!. Be social and share it with social media, if you feel worth sharing it.