Log4Shell, a critical security flaw in Log4j, an open-source logging software used in everything from online games to enterprise software and cloud data centers, has security teams all over the world scrambling to fix it. Because of its widespread use, the internet has been put on high alert as hackers increase their efforts to target weak systems. A flaw in Log4j, a Java library for logging error messages in applications, is the most high-profile security vulnerability on the internet right now and comes with a severity score of 10 out of 10.
The library is developed by the open-source Apache Software Foundation and is a key Java-logging framework. CVE-2021-44228, a remote code execution flaw in Log4j, was already being exploited in the wild, warnings have been issued by several national cybersecurity agencies, including the Cybersecurity and Infrastructure Security Agency (CISA) and the UK’s National Cyber Security Centre (NCSC).
It includes libraries that are used by large software development companies that are used across the enterprise, including Amazon, Apple, Cisco, Cloudflare, Tesla, Twitter, and yes, VMware.
The bad thing is this vulnerability is literally everywhere and a patched version of code is not available as of yet to all products that are using it, which is dangerous. Most likely due to its popularity and prevalence everywhere, it will be actively exploited over the next few days by attackers.
As per the VMSA-2021-0028, below VMware products are also affected. VMware is continuously working towards releasing the patches and Workaround instructions to address the vulnerability CVE-2021-44228 in VMware products. All the information can be tracked here
https://www.vmware.com/security/advisories/VMSA-2021-0028.html
1. Impacted Products (Under Evaluation)
- VMware Horizon
- VMware vCenter Server
- VMware HCX
- VMware NSX-T Data Center
- VMware Unified Access Gateway
- VMware WorkspaceOne Access
- VMware Identity Manager
- VMware vRealize Operations
- VMware vRealize Operations Cloud Proxy
- VMware vRealize Automation
- VMware vRealize Lifecycle Manager
- VMware Site Recovery Manager, vSphere Replication
- VMware Carbon Black Cloud Workload Appliance
- VMware Carbon Black EDR Server
- VMware Tanzu GemFire
- VMware Tanzu Greenplum
- VMware Tanzu Operations Manager
- VMware Tanzu Application Service for VMs
- VMware Tanzu Kubernetes Grid Integrated Edition
- VMware Tanzu Observability by Wavefront Nozzle
- Healthwatch for Tanzu Application Service
- Spring Cloud Services for VMware Tanzu
- Spring Cloud Gateway for VMware Tanzu
- Spring Cloud Gateway for Kubernetes
- API Portal for VMware Tanzu
- Single Sign-On for VMware Tanzu Application Service
- App Metrics
- VMware vCenter Cloud Gateway
- VMware vRealize Orchestrator
- VMware Cloud Foundation
- VMware Workspace ONE Access Connector
- VMware Horizon DaaS
- VMware Horizon Cloud Connector
- VMware NSX Data Center for vSphere
- VMware AppDefense Appliance
- VMware Cloud Director Object Storage Extension
- VMware Telco Cloud Operations
- VMware vRealize Log Insight
- VMware Tanzu Scheduler
- VMware Smart Assurance NCM
- VMware Smart Assurance SAM [Service Assurance Manager]
- VMware Integrated OpenStack
- VMware vRealize Business for Cloud
- (Additional products will be added)
Workaround for Apache Log4j Vulnerability(CVE-2021-44228 ) in vCenter Server Appliance
NOTE:
VCHA needs to be removed before executing the steps in this KB article.
Environments with external PSCs need to have the script executed on both vCenter and PSC appliances.
Steps for Applying Workaround:
- Take the snapshot of your vCenter Server Appliance
- Download the script attached the VMware KB 87088 (vmsa-2021-0028-kb87081.py)
- Transfer the file to /tmp folder on vCenter Server Appliance using WinSCP or follow the below steps to copy paste the script contents to VCSA using Putty
- Login to the vCSA using an SSH Client (using Putty.exe or any similar SSH Client)
- Open the script on your desktop in Notepad (Notepad++ is preferred)
- Copy the entire contents (Ctrl + C)
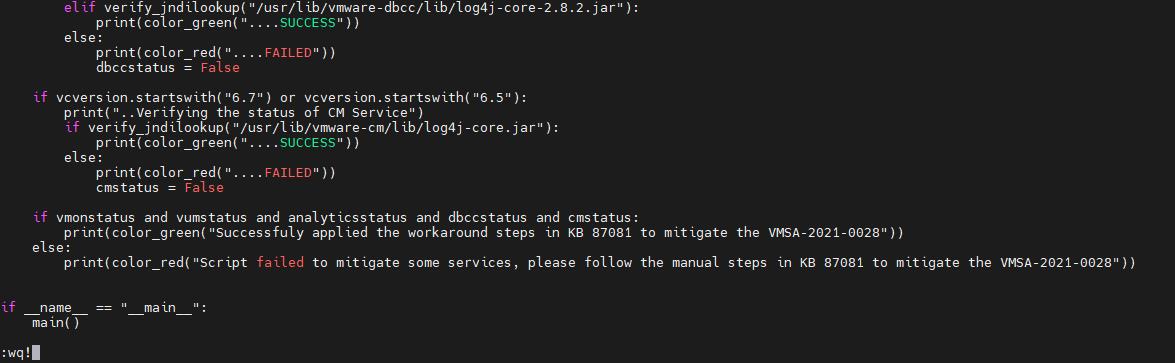
- On VCSA, create a new file using vi command
- vi /tmp/vmsa-2021-0028-kb87081.p
4. Press the ‘Insert’ button on the keyboard to insert the contents
5. Right-click on the screen to Paste the script contents Copied from the previous step
6. Save the Contents using Keys (Press Esc and then :wq! followed by Enter key)
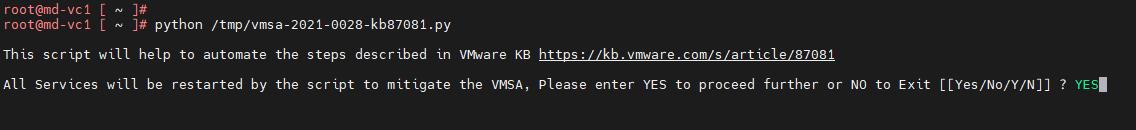
8. Script will prompt for users input to confirm the services restart as all the services needs to be restarted to implement the workaround, Enter ‘y’ or ‘Y’ if you want to proceed with the script
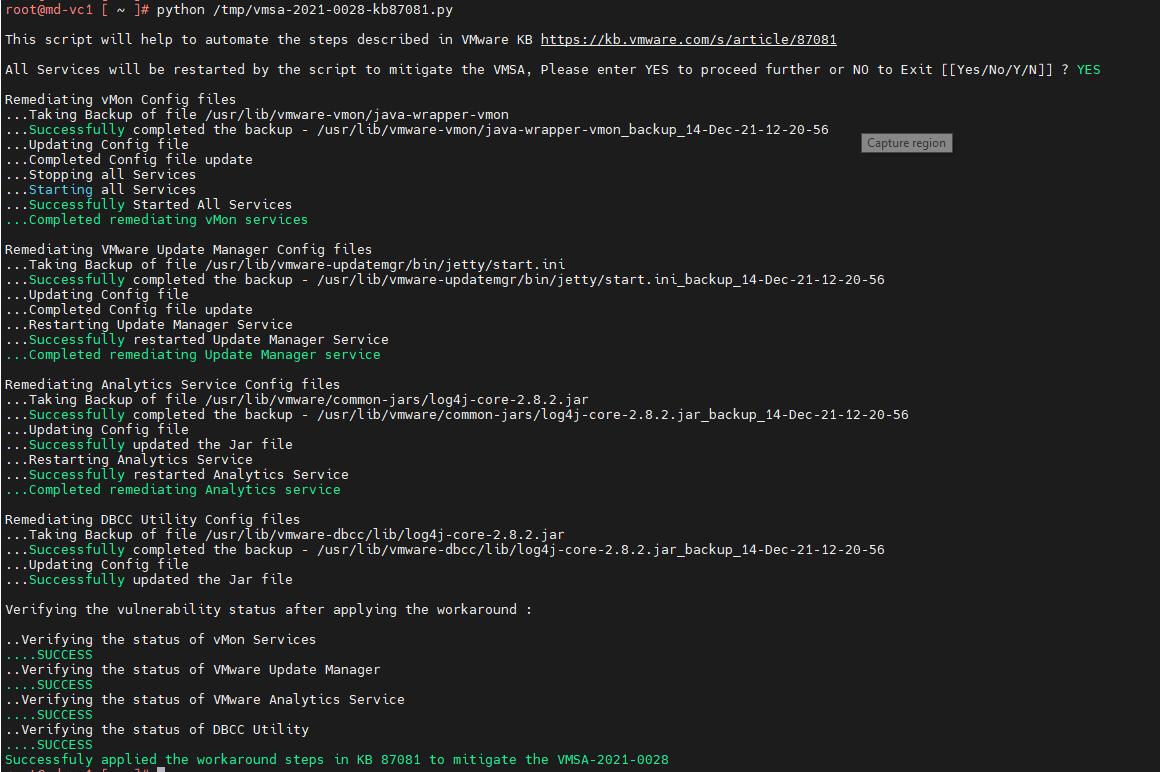
9. Script will proceed further and the status will be displayed on the screen, sample screenshots for successful executions are available in Related Information of this KB.
VMware has simplified the workaround for Log4j in the vCenter Server appliance with a simple python script. Which takes care of applying the workaround for the Log4j vulnerabilities in the vCenter Server Appliance. I hope this article is informative for you. Thanks for reading!!!. Be social and share it on social media, if you feel worth sharing it.