A segment, formerly known as a logical switch, reproduces switching functionality in an NSX-T Data Center virtual environment completely decoupled from the underlying hardware. Virtual machines can be connected to the NSX-T segments as similar to how we attach the VM network adapter to virtual port groups. The VMs can then communicate with each other over tunnels between hypervisors if the VMs are connected to the same segment. In the previous article, we have discussed how to create NSX-T segments and how to migrate the VM network to N-VDS (NSX-T segments). We have connected multiple virtual machines to different NSX-T segments and we will validate connectivity between VM’s in NSX-T segments without deploying the NSX-T Tier 1 router(aka Logical router).
I have deployed 3 Tier application and I have 4 different virtual machines for web, app and DB tier VM’s for this demo.
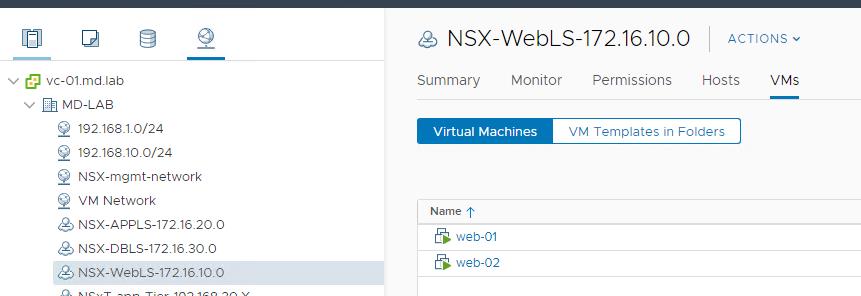
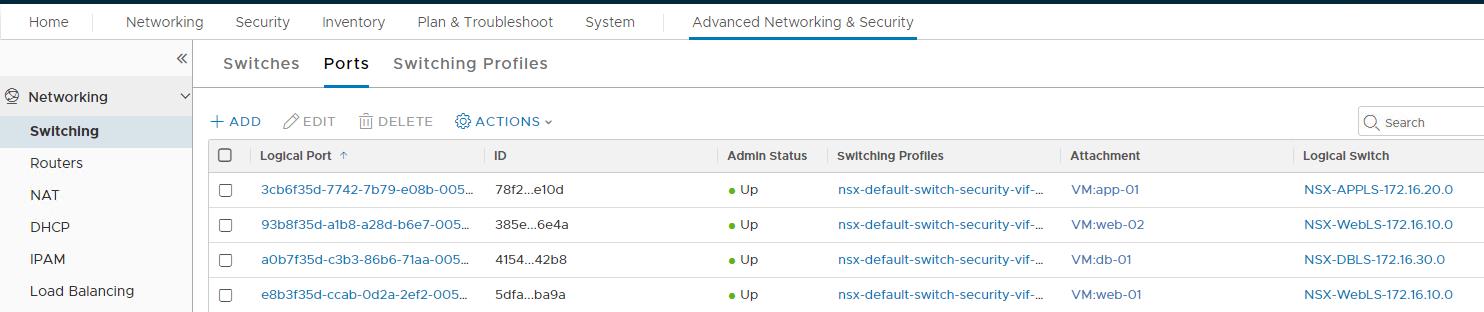
The virtual machines “web-01” and “web-02” connected to the NSX-T segment called “NSX-WebLS-172.16.10.0”.
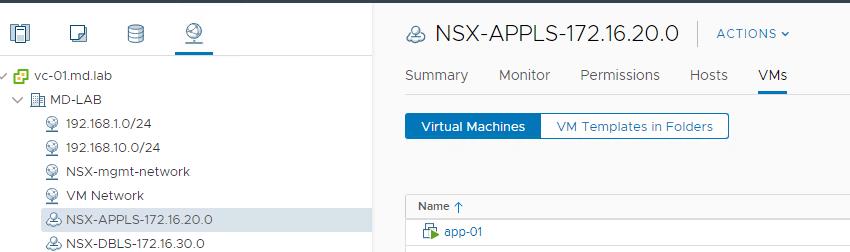
“App-01” virtual machine connected to the NSX-T segment called “NSX-APPLS-172.16.20.0”.
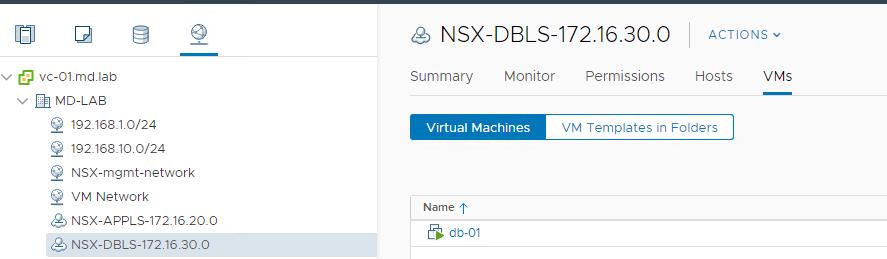
“DB-01” virtual machine connected to the NSX-T segment called “NSX-DBLS-172.16.30.0”.
Navigate to Advanced Networking & Security >Switching > Ports and verify that the logical ports are created with Admin Status and Operational Status as Up. we can also check the respective logical switch in which VM’s are connected under the “Attachment” option.
Validate connectivity between VM’s in NSX-T segments
Let’s validate the connectivity between VM’s in NSX-T segments. At this stage, we didn’t deploy NSX-T Tier 1 router (Logical router) to establish the routing across the NSX-T segments. The expected result is VM’s connected in the same segments should be able to ping each other and VM’s connected to different NSX-T segments cannot ping each other.
Below are the IP address of each of VM’s
Web-01 -> 172.16.10.11 (Connect to segment “NSX-WebLS-172.16.10.0”)
Web-02 -> 172.16.10.12 (Connect to segment “NSX-WebLS-172.16.10.0”)
App-01 -> 172.16.20.11 (Connect to segment “NSX-APPLS-172.16.20.0”)
DB-01 -> 172.16.30.11 (Connect to segment “NSX-DBLS-172.16.30.0”)
Ping Tests :
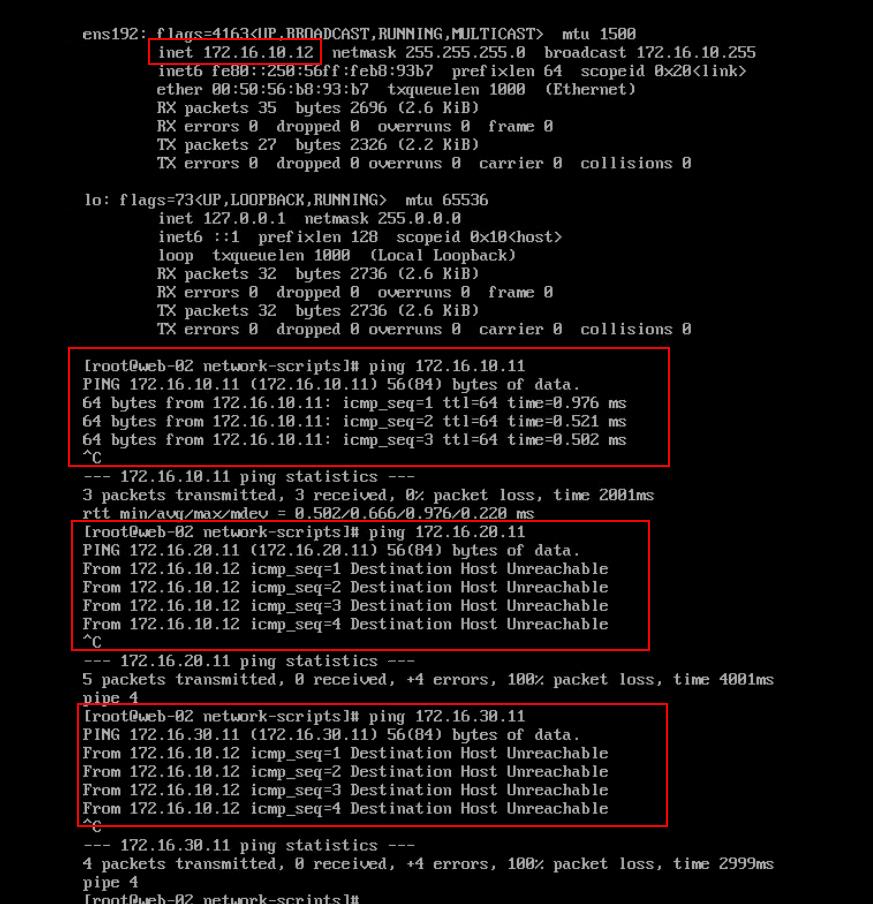
Ping between Web VM’s (Web-01 & web-02) 172.16.10.12 to 172.16.10.11 connect in the same segment is successful
Ping between the virtual machine web-02 (172.16.10.11) and app-01 (172.16.20.11) connected in different segments is failed (Destination Host Unreachable)
Ping between the virtual machine web-02 (172.16.10.11) and DB-01 (172.16.30.11) connected in different segments is failed (Destination Host Unreachable)
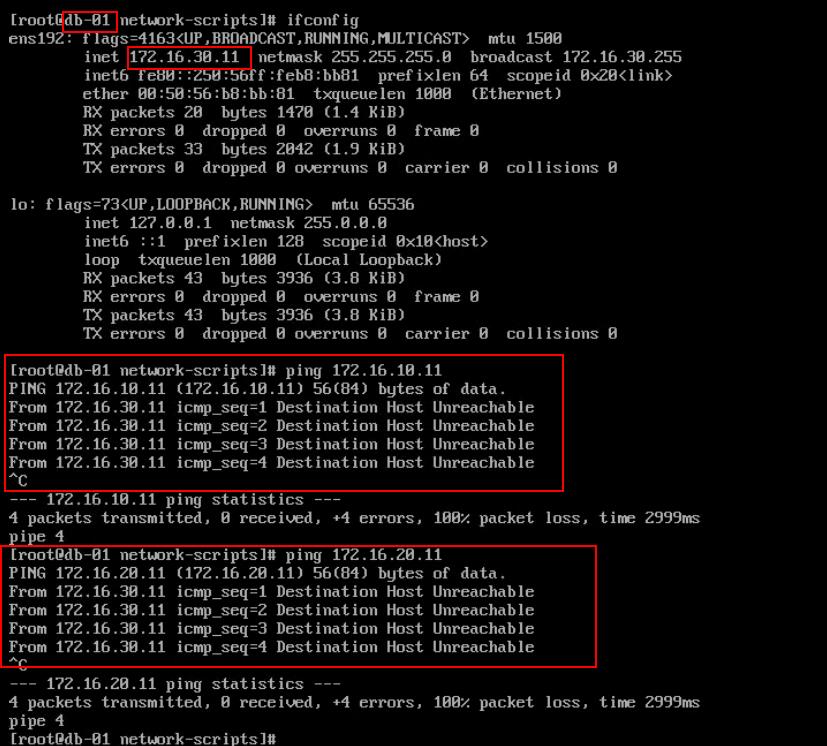
Ping between the virtual machine DB-01 (172.16.30.11) and Web-01 (172.16.10.11) connected in different segments is failed (Destination Host Unreachable)
Ping between the virtual machine DB-01 (172.16.30.11) and App-01 (172.16.20.11) connected in different segments is failed (Destination Host Unreachable)
So our observation in the network connectivity test between the VM’s connected in the same segment and the different segments is VM’s connected in the same segments are able to ping each other and VM’s connected to different NSX-T segments cannot ping each other. Segments are like VLAN in the network switch. We need a router to provide routing between different VLANs. So we need a Logical router (NSX-T T1 router) to provide routing between the NSX-T segment.
In the upcoming posts, we discuss how to deploy NSX-T T1 router and provide routing across the NSX-T segments. I hope this is informative for you. Thanks for reading!!!. Be social and share it in social media, if you feel worth sharing it.